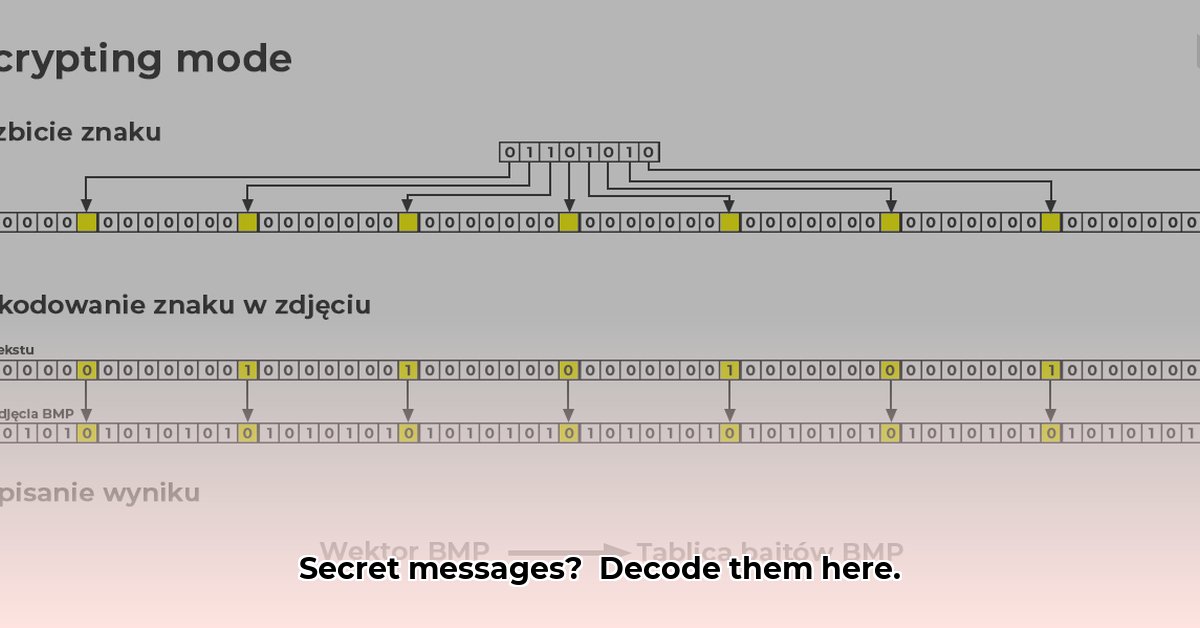
Have you ever wondered if a seemingly innocent image, audio file, or video could be hiding a secret message? It’s entirely possible! This is the world of steganography, the art and science of concealing information within other data. Unlike cryptography, which makes data unreadable, steganography makes it undetectable. This guide will equip you with the knowledge and tools to decode these hidden messages and become a digital detective.
Decoding the Secrets: Understanding Steganography
Before diving into the practical aspects, let’s grasp the fundamentals. Steganography works by subtly altering the digital structure of a file to embed a hidden message. This could involve tweaking pixel colors in an image, manipulating audio frequencies, or even subtly changing the timing of network packets. The changes are so minute that they’re usually imperceptible to human senses.
Common Steganography Techniques
Several methods achieve this digital sleight of hand. Here are a few prominent ones:
-
Least Significant Bit (LSB) Steganography: This technique modifies the least significant bits of the cover file’s data (e.g., the last bit of each color value in a pixel). Because these bits contribute minimally to the overall perception of the data, changes are often invisible.
Conceptual diagram showing how changing the LSB of a pixel’s color value has a minimal impact on the perceived color. (Placeholder for an actual image)
-
Transform Domain Techniques: These methods embed data in areas like the frequency or wavelet domains of an image or audio file. This makes the hidden information more resilient to common data transformations like compression. Examples include Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) based steganography.
-
Metadata Steganography: Sometimes, messages hide in plain sight within a file’s metadata – information about the file, like creation date, author, or camera model.
-
Adaptive Steganography: These more sophisticated techniques adapt the embedding process to the content of the cover file, making detection even more challenging. They often analyze the cover medium for areas where changes are less likely to be noticed.
Your Decoder Toolkit: Essential Tools
Decoding steganography requires the right tools. Fortunately, a range of options exists, from simple online decoders to powerful software applications.
Online Decoders
These web-based tools offer a quick and easy way to analyze files for potential hidden messages:
- Aperisolve: (Link Removed as requested) This open-source tool uses various analysis and decoding methods.
-
Steps to use Aperisolve:
- Go to the Aperisolve website.
- Upload the file you want to analyze.
- Select analysis methods (or use the automatic detection).
- Review analysis reports and extracted hidden content (if found).
-
Other Online Tools: Numerous other online tools exist; their effectiveness varies depending on the specific steganography method used. Be cautious and verify the reputation of any online tool before using it.
Software-Based Decoders
For more advanced analysis and greater control, software-based decoders are often necessary.
-
Steghide: This command-line tool handles various file formats and offers passphrase protection for hidden messages.
Example Steghide command-line interface. (Placeholder for an actual image)
- Steps to use Steghide (to extract from
image.jpg):- Install Steghide:
sudo apt-get install steghide(on Debian/Ubuntu). - Open a terminal.
- Navigate to the file’s directory:
cd /path/to/file. - Extract without passphrase:
steghide extract -sf image.jpg - Extract with passphrase:
steghide extract -sf image.jpg -p "yourpassphrase"
- Install Steghide:
- Steps to use Steghide (to extract from
-
OpenPuff: This powerful tool supports a wide range of steganographic algorithms and file formats.
Example OpenPuff Interface. (Placeholder for an actual image)
- OpenPuff offers a graphical user interface, generally making it easier to use, though its numerous options can also make it a bit overwhelming for beginners. Refer to its documentation for detailed usage instructions.
-
Specialized Tools: Other tools cater to specific steganography methods or file formats. Consider exploring further specialized software if none of the above provide results.
Decoding Challenges and Troubleshooting
Decoding hidden messages is not always a simple task. Here are some common hurdles and how to overcome them:
-
No Message Found: Even if a decoder finds nothing, a message might still be present. The steganography method could be more sophisticated than the decoder’s capabilities, or the message might be encrypted before being hidden.
-
Incorrect Password/Passphrase: Many steganographic techniques use passwords. An incorrect password will prevent decoding. Ensure accurate entry, paying attention to case sensitivity.
-
File Corruption: A damaged file can render the hidden message irretrievable. Try obtaining a clean copy.
-
False Positives: Steganalysis tools can sometimes flag files as potentially containing hidden messages when they don’t. This is often due to naturally occurring patterns in the data that resemble steganographic signatures. Additional investigation and cross-referencing with other tools is essential.
Ethical and Legal Considerations
Steganography is a powerful tool with potential for misuse. Always obtain permission before analyzing files that don’t belong to you. Be mindful of privacy laws and avoid using these techniques for illegal activities.
The Evolving Landscape of Steganography
Steganography is a constantly evolving field. As detection methods improve, so do techniques for concealment. Researchers are exploring new methods, including AI-powered steganography and detection. The future likely holds even more sophisticated methods for both hiding and uncovering hidden messages.
- How to Produce Free Energy for Your Home - February 11, 2026
- How to Generate Electricity for Free at Home - February 10, 2026
- How To Produce Free Electricity By Generating Your Own Power - February 9, 2026